The strength of a blockchain comes from the collaboration of thousands of nodes working together to keep everything aligned, secure, and running without interruption.
Each type of node contributes in a different way — some enforce rules, others store complete histories, and many ensure broad accessibility.
Understanding these functions is more than helpful: it’s essential for anyone building, researching, or creating solutions within Web3.
In this article, you’ll explore the main types of blockchain nodes, how each one operates, and when they make a real impact in practice.
What Is a Blockchain Node?
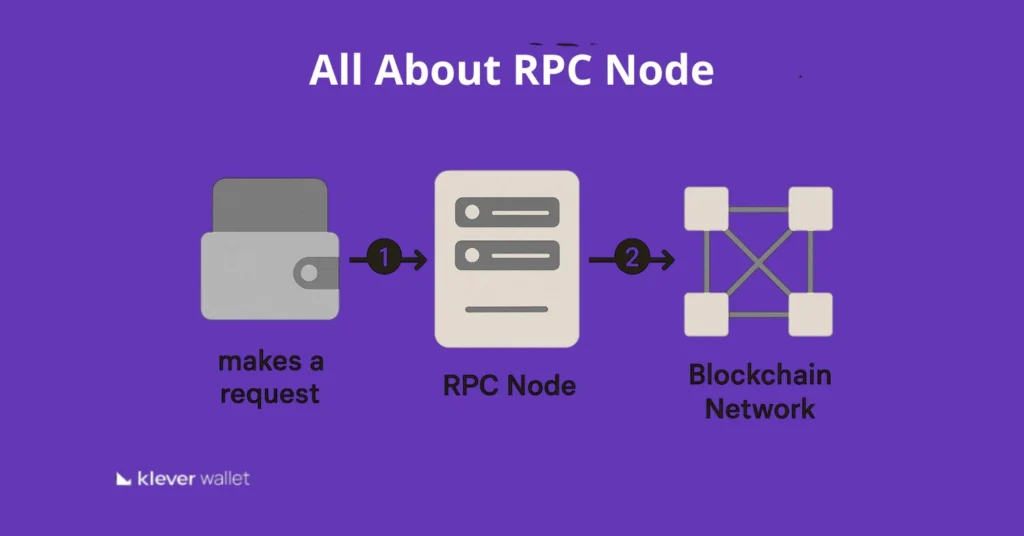
A blockchain node is a connection point within a blockchain network that receives, stores, verifies, and relays information, ensuring that all participants access the same data accurately.
In practice, a node can:
- Store parts of the chain or the full transaction history, depending on its type.
- Verify transactions and blocks, checking signatures, balances, and protocol rules.
- Relay data to other nodes, helping the network stay synchronized.
- Contribute to consensus, when acting as a validator (PoS) or miner (PoW).
Having many independent nodes prevents the ledger from being concentrated in a single place, reducing risks of failures, censorship, or unauthorized changes. This diversity is what upholds the reliability and security of any blockchain.
Why Blockchain Nodes Matter
Nodes provide:
- security: multiple independent copies prevent tampering or unauthorized changes
- redundancy: the network continues even if some nodes go offline
- transparency: anyone can verify past transactions
- reliability: blocks and transactions follow the protocol rules
A blockchain with more distributed nodes is harder to censor, attack or shut down.
Main Types of Blockchain Nodes
1. Full Nodes
Full nodes store the entire blockchain and independently validate every block and transaction. They enforce protocol rules and reject any invalid data.
Characteristics
- Complete copy of the blockchain: they keep the full history from the genesis block.
- Independent validation: they confirm blocks and transactions on their own, without relying on external sources.
- Foundation of network security: they prevent fraud, detect inconsistencies, and strengthen decentralization.
Use Cases
Full nodes are essential for users who need maximum accuracy and trust:
developers, researchers, validators, companies that rely on on-chain auditing, and anyone who wants to verify everything directly from the source.
Variations of Full Nodes
All full nodes validate blocks independently, but they can operate with different storage levels. The two most common variations are Pruned Nodes and Archive Nodes.
1.1 Pruned Full Node
A pruned node downloads the entire blockchain at first but later discards older blocks to reduce storage usage.
It keeps only the essential data needed to validate new transactions and blocks.
This approach allows users with limited storage to still participate as rule-enforcing nodes, strengthening decentralization even without keeping the full history.
1.2 Archive Node
Archive nodes store everything: full blocks, transactions, and every historical state of the blockchain — including old states that were overwritten over time.
They are indispensable for applications that require complete datasets, such as:
- Blockchain explorers (Etherscan, Solscan).
- On-chain analytics tools.
- Indexers that build advanced databases.
- Debugging and historical reconstruction for researchers and developers.
These nodes require very large storage capacity, especially in networks with heavy smart-contract activity like Ethereum.
2. Light Nodes (Light Clients / SPV Nodes)
Light nodes are streamlined versions of full nodes. Instead of storing the entire blockchain, they keep only block headers — the minimum required to verify whether a block is valid.
Whenever they need more detailed data, like a full transaction, they request it from full nodes.
They don’t validate the entire chain independently but use simplified methods (such as SPV, Simplified Payment Verification) to confirm whether a transaction was included in a valid block.
Why They Matter
- Ideal for digital wallets: they work well on phones and devices with limited memory and processing power.
- Fast synchronization: they download only a fraction of the data.
- Lower barrier to Web3: users can interact with the blockchain without running full infrastructure.
- Core of modern wallets: most crypto wallets rely on light clients.
3. Validator Nodes (Proof-of-Stake)
Validator nodes maintain order and security in Proof-of-Stake (PoS) blockchains.
Instead of competing with computational power like in PoW, these nodes validate, propose, and attest blocks based on the number of tokens committed as staking.
To operate, a validator must lock a specific amount of the network’s tokens. This deposit acts as a guarantee of good behavior: the larger the stake, the higher the chance of being chosen to produce a block.
Main Responsibilities
- Validate blocks: checking transactions and ensuring protocol rules are followed.
- Propose new blocks: when selected by the algorithm, they assemble the next block.
- Maintain constant uptime: they must stay online to avoid penalties or missed rewards.
- Prevent protocol violations: actions like signing conflicting blocks or staying offline for long periods can result in slashing (loss of part of the stake).
Use Cases
- Users who stake and want to directly support network security.
- Institutions, exchanges, and infrastructure providers.
- Specialized services that run validators on behalf of clients.
- Anyone seeking rewards while helping maintain blockchain integrity.
4. Mining Nodes (Proof-of-Work)
Mining nodes create new blocks in Proof-of-Work (PoW) blockchains.
They compete to solve complex mathematical puzzles — the mining process.
The first node to find a valid solution earns the right to add the next block.
To do this, miners use high-performance machines running cryptographic hashing algorithms that demand heavy energy and computational resources.
This effort forms the core of PoW security: manipulating the chain would require replicating massive mining power, which is extremely costly.
Key Characteristics
- Specialized hardware: ASICs and GPUs dominate due to their superior hashing performance.
- High security: the cost to attack or dominate the network becomes prohibitively expensive.
- Financial rewards: miners receive block rewards and transaction fees for sustaining the network.
5. Masternodes
Masternodes appeared in earlier blockchain designs as an additional layer of functionality beyond standard nodes.
They don’t create blocks like miners but take on special tasks that improve network features.
Operating a masternode usually requires locking a fixed amount of tokens as collateral.
This deposit represents an economic commitment: the more value locked, the more incentive the operator has to behave correctly.
Main Functions
- Instant transactions: some networks use masternodes to confirm operations faster.
- Governance: operators often receive voting rights on protocol decisions.
- Advanced validation: depending on the network, they may store specific data, support privacy features, or run additional checks.
Masternodes were common in projects like Dash and PIVX, which aimed to balance security, speed, and governance.
6. Authority Nodes (Permissioned Blockchains)
Authority nodes are used in permissioned blockchains — environments where only approved participants can validate or produce blocks.
They are widely adopted in corporations, financial institutions, consortiums, and organizations that need strict governance and auditability.
Unlike public blockchains, where anyone can run a node, permissioned networks require verified identity and explicit authorization to join the validation process.
Main Functions
- Permission-based validation: only approved operators can verify transactions and approve blocks.
- Certified identity: each authority is known and auditable, supporting accountability.
- Controlled block production: the protocol defines which entities can create and sign blocks.
- Regulatory compliance: suitable for networks that require formal governance and operational safety.
These nodes appear in enterprise solutions such as Hyperledger Fabric, Quorum, and private financial-sector networks where trust between participants must be formalized.
Which Node Type Should You Use?
| Node Type | Storage Needs | Ideal For | Strength |
| Full Node | High | Developers, power users | Independent validation |
| Pruned Node | Medium | Users w/ limited storage | Network support without full history |
| Archive Node | Very high | Explorers, analytics, institutions | Complete historical data |
| Light Node | Low | Wallets, mobile apps | Fast access |
| Validator Node | Medium/high | PoS staking | Network security + rewards |
| Mining Node | High (PoW) | Miners | New block creation |
| Masternode / Authority Node | Varies | Governance or permissioned networks | Specialized roles |
Why Blockchain Needs Multiple Node Types
No single type of node can handle all the requirements of a modern blockchain. Each model — full, light, validator, miner, or archive — plays a complementary role that balances performance, security, accessibility, and depth of data.
For the network to operate efficiently and reliably, different nodes take on specific responsibilities:
- Full nodes ensure all protocol rules are enforced correctly, rejecting invalid blocks and transactions.
- Light nodes allow millions of users to access blockchain technology with everyday devices, without heavy infrastructure.
- Validators and miners create new blocks and maintain consensus, ensuring the chain continues securely.
- Archive nodes preserve the complete history, enabling audits, on-chain analytics, indexing, and advanced research.
When these nodes operate together, the network becomes:
- More stable, thanks to distributed validation.
- More transparent, as data remains complete and verifiable.
- More resilient, avoiding single points of failure or control.
This combination is what allows blockchains to grow, support new users, and remain secure over time.
The Network Exists Only Because Each Blockchain Node Fulfills Its Role
A blockchain’s architecture stays intact because different types of nodes work together.
Combined, they create an infrastructure that is reliable, auditable, and resistant to failures.
Understanding how blockchain nodes work together helps professionals, developers, and researchers build more secure solutions and make better use of modern blockchain capabilities — including ecosystems like Klever, which continue to evolve to deliver speed, security, and ease of use.