
As the adoption of cryptocurrencies accelerates, so do the cybersecurity threats targeting users and their digital assets. One of the most dangerous and stealthy threats is the crypto malware scam—a form of malicious software that targets cryptocurrency users with the goal of stealing funds, mining coins using victim resources, or compromising wallet credentials.
Unlike crypto scams that rely on persuasion or fake giveaways, crypto malware operates silently, often without any obvious warning signs. This article covers what crypto malware is, how it differs from ransomware, how it spreads, warning signs to look for, real-world case studies, and effective prevention strategies.
What Is Crypto Malware?
Crypto malware is a type of financially motivated malware designed to exploit cryptocurrency users. It infects devices or applications to achieve one of the following:
- Illicitly mine cryptocurrencies like Monero (cryptojacking)
- Steal wallet credentials, private keys, or seed phrases
- Replace wallet addresses during transactions (clipboard hijacking)
Crypto malware can affect desktops, mobile devices, browser extensions, and even smart contracts. It spreads through phishing, fake apps, compromised software packages, and malicious browser tools.
How Crypto Malware Differs from Ransomware
Both crypto malware and ransomware involve cryptocurrency, but their methods and impact differ.
| Feature | Crypto Malware | Ransomware |
| Primary Objective | Steal or generate cryptocurrency silently | Lock files and demand ransom in cryptocurrency |
| Visibility | Hidden, often goes unnoticed | Highly visible with ransom message displayed |
| Common Attack Vector | Fake wallet apps, browser extensions, clipboard tools | Email attachments, software vulnerabilities |
| Payment Model | Gains profit through mining or wallet theft | Demands crypto payment for decryption key |
| Impact | Device slowdown, data theft, unauthorized transactions | File loss, operational disruption, extortion |
Ransomware is overt and immediate. Crypto malware is covert, often persisting for weeks or months before being detected.
How Crypto Malware Spreads
1. Email Phishing Attachments
Attackers craft emails posing as crypto services or exchanges. These emails carry malicious attachments or links that, once opened, install malware onto the user’s system. Common tactics include fake “account suspension” warnings or “wallet verification” requests.
2. Malicious Browser Extensions
Fake browser extensions impersonate legitimate tools and silently access wallet data, clipboard contents, or browser sessions. Some inject malicious scripts into visited websites or hijack wallet connections to DApps.
3. Fake Wallet or Trading Apps
Disguised as legitimate apps, these malicious wallets prompt users to input private keys or seed phrases, which are then sent to attackers. They often appear on unofficial APK sites or occasionally slip into official app stores.
4. Fake Airdrops and “Support” Chats
Social engineering plays a significant role in malware delivery. Scammers posing as support staff or project admins direct users to install tools or visit phishing sites under the guise of helping with an issue or offering free tokens.
5. Compromised Websites (Watering Hole Attacks)
Attackers compromise popular crypto-related websites and inject malicious scripts that auto-download malware or exploit browser vulnerabilities. These are hard to detect and don’t require user interaction beyond visiting the site.
Crypto Malware on Mobile Devices: Special Risks
Smartphones are convenient tools for managing crypto, but they also present unique vulnerabilities:
- Android users face higher risk due to APK side loading and less restrictive permissions.
- iOS users are safer by design but can still fall victim to social engineering and TestFlight-based attacks.
- Most users keep wallets and 2FA apps on the same device, making compromise especially dangerous.
Signs of mobile malware include overheating, rapid battery drain, sudden app crashes, unexpected requests for seed phrases, and clipboard manipulation.
Crypto Malware in the Software Supply Chain
Crypto malware doesn’t always reach users directly. Sometimes, hackers target the tools and software that developers use to create crypto apps. If these tools are infected, the malware can spread to many users through app updates without anyone noticing.
Infected Open-Source Libraries
Attackers upload malicious packages to public repositories like npm or PyPI. These libraries mimic legitimate ones and, once integrated, can steal wallet data or inject backdoors.
Compromised CI/CD Pipelines
Malware inserted into build environments can go unnoticed during development and get deployed through regular updates, affecting thousands of users.
Poisoned App Updates
Fake or hijacked update servers can push malicious software instead of legitimate patches. In crypto, this is especially dangerous due to the trust users place in wallet software.
Third-Party SDKs and APIs
Malicious SDKs embedded in wallet apps or DApps can silently exfiltrate data, replace wallet addresses, or trigger unauthorized transactions.
Real-World Cases of Crypto Malwares: 2020–2025
SparkCat – The Malware That Bypassed App Store Security (2025)
Discovered by Kaspersky, SparkCat is a sophisticated malware that uses Optical Character Recognition (OCR) technology to scan images stored on Android and iOS devices.
It targets cryptocurrency wallet recovery phrases and other sensitive information found in screenshots and saved photos.
The malware disguises itself as seemingly legitimate apps, such as messaging platforms or delivery services, and has even made its way into official stores like Google Play and the App Store. Once it gains access to the photo gallery, SparkCat extracts the confidential data and sends it to servers controlled by cybercriminals.
Qakbot Malware Takedown (2025)
In 2025, U.S. authorities seized $24 million from a key developer of the Qakbot botnet, one of the most persistent and dangerous malware infrastructures in recent history. Active since 2008, Qakbot evolved from a banking trojan into a multifunctional tool used by cybercriminals to distribute ransomware, steal financial data, and harvest credentials — including access to cryptocurrency wallets. The takedown marked a major disruption of a long-running cybercrime network.
Lumma Stealer Malware Disruption (2025)
In a coordinated international effort in 2025, law enforcement agencies dismantled the Lumma Stealer operation — a powerful infostealer available in Russian websites since 2022, that specifically targeted browser-based cryptocurrency wallets and browser extensions. The malware as a service (Maas) had infected nearly 400,000 systems globally, silently collecting private keys, login credentials, and wallet data, posing a serious threat to users across multiple platforms.
MetaMask Browser Extension Phishing (2021)
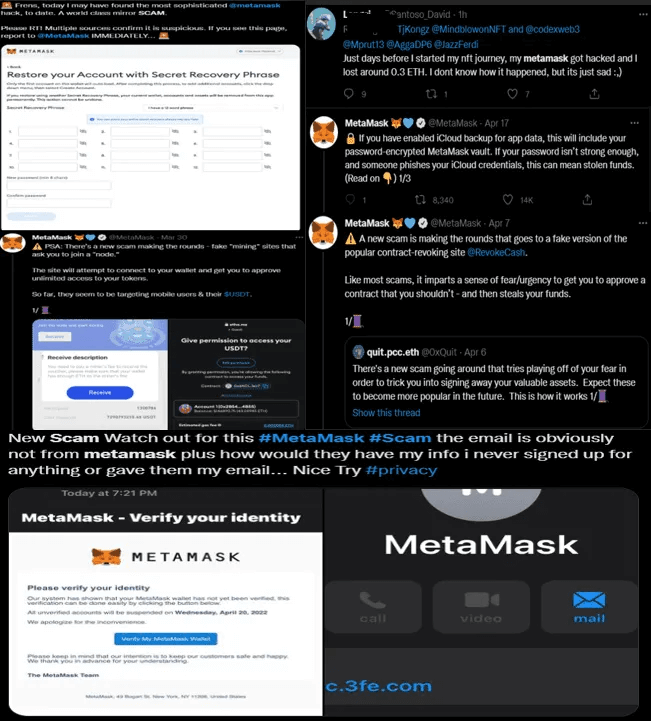
Source: cyble
In 2021, cybercriminals cloned the official MetaMask website and used paid ads in search engine results to direct users to a fake version. Victims were tricked into installing counterfeit browser extensions or connecting their wallets to fraudulent decentralized applications (DApps), resulting in stolen seed phrases and unauthorized transfers of crypto assets.
Electrum Wallet Malware Campaign (2020–2021)
Between 2020 and 2021, attackers exploited a vulnerability in Electrum’s update system to redirect users to malicious servers. These servers prompted users to install a fake software update, which included malware designed to steal wallet credentials. This campaign reportedly led to the theft of millions of dollars in Bitcoin from unsuspecting users.
Ledger Data Breach (2020)

In 2020, Ledger — a leading hardware wallet manufacturer — experienced a major data breach involving a third-party service provider. Although no wallets were technically compromised, the exposed personal data of over 270,000 customers was used in phishing campaigns. Victims received emails containing fake firmware updates laced with malware that aimed to steal their wallet credentials.
Clipper Malware on Google Play (2019)
In February 2019, cybersecurity researchers at ESET discovered the first known instance of clipboard-hijacking malware on the official Google Play Store. Disguised as the MetaMask app, the malware—identified as Android/Clipper.C—monitored users’ clipboard activity and silently replaced copied cryptocurrency wallet addresses with those controlled by attackers. As a result, users unknowingly transferred funds to fraudulent wallets. This incident underscored the fact that even trusted app marketplaces are not immune to sophisticated malware threats.
Supply Chain Attack: Copay Wallet (2018)
While older, the 2018 Copay wallet incident remains a critical case in supply chain security. A malicious version of an open-source JavaScript library (event-stream) was injected into the app’s codebase and pushed as an official update. This compromised version leaked user wallet credentials upon execution, highlighting the long-term risks of dependency poisoning.
Related Threat: Crypto Extortion Beyond Malware
Though not based on software, physical and psychological extortion has become more common. Criminals have targeted known crypto holders with threats, home invasions, and kidnappings to force transfers of digital assets. This highlights that true crypto security extends beyond devices — it also requires protecting your identity and behavior.
How to Protect Against Crypto Malware
Use Official Sources
Only download wallets and extensions from verified sources. Never trust links sent via social media or chat groups.
Secure Your Seed Phrase
Never enter your seed phrase unless restoring a wallet. Never store it digitally (e.g., screenshots, notes apps, cloud drives).
Enable 2FA and Use Hardware Wallets
Two-factor authentication and hardware wallets offer strong protection against both remote and malware-based attacks.
Monitor Device Behavior
Watch for unusual activity like high CPU usage, overheating, battery drain, or unauthorized transactions.
Keep Software Updated
Regularly update operating systems, wallet apps, and browser extensions to patch known vulnerabilities.
Revoke Unused DApp Permissions
Use tools like revoke.cash to audit and remove unnecessary smart contract approvals.
What to Do If You’re Infected by Crypto Malware
If you suspect you’ve been infected with crypto malware, take these steps immediately to minimize damage:
1. Disconnect from the Internet
Cut off the compromised device from the network to stop ongoing malicious activity or data exfiltration.
2. Move Your Funds Securely
If you still have access, use a clean (uninfected) device to transfer your funds to a newly created wallet with a new seed phrase.
3. Change All Credentials
Reset passwords on all linked accounts and enable 2FA on services where it’s missing.
4. Back Up Critical Files Safely
Copy important files to an external drive, but avoid running any potentially infected programs.
5. Wipe and Reinstall the Operating System
Perform a clean OS installation to remove any deeply embedded malware.
6. Scan Reinstalled Software
Use trusted antivirus and antimalware tools to check any files or programs before reinstalling.
7. Report the Incident
Notify relevant platforms or developers if the malware came through third-party apps, extensions, or compromised websites.
Securing Your Crypto: What You Need to Know
Crypto malware continues to evolve in both sophistication and scale, targeting users through stealthy tactics and increasingly creative vectors. From fake wallet apps and browser extensions to compromised supply chains, the threat landscape demands constant vigilance.
The rise in targeted attacks—from clipboard hijackers to infostealers—makes it clear that simply holding cryptocurrency isn’t enough. You must also protect it proactively. Maintaining strong operational security, using trusted software, and understanding the red flags of malware behavior are now non-negotiable.
Whether you’re a developer, investor, or everyday user, building habits around digital hygiene and wallet security is the most effective way to guard against theft. In the crypto world, security is not a feature—it’s a responsibility.
Be Klever.




