
Crypto Phishing Scams remain one of the most deceptive and damaging threats in the cryptocurrency space with severe consequences.
Once an attacker gains access to a user’s funds, the theft is often irreversible. Whether through fake websites, fraudulent emails, or impersonation scams, phishing attacks continue to evolve, making them harder to detect and easier to fall for.
This guide will equip you with the knowledge needed to recognize phishing attempts in cryptocurrency, to protect your assets, and take immediate action if you become a target.
Definition of Phishing Scams
Phishing scams are fraudulent attempts to steal sensitive information — like passwords, seed phrases, or private keys — by impersonating a trusted source. In the crypto world, scammers often pose as exchanges, wallet providers, or support teams to trick users into revealing confidential data or signing malicious transactions.
It’s also the most common form of cybercrime globally. Every day, over 3.4 billion spam emails are sent, with phishing accounting for a significant share.
The consequences can be devastating, with irreversible transactions and lost funds are nearly impossible to recover.
In the crypto space, phishing often targets wallets, exchanges, and DeFi platforms, tricking users into revealing private keys or signing malicious transactions.
Phishing in Crypto Statistics
Globally, Google blocks around 100 million phishing emails each day, and over 48% of all emails in 2022 were spam. Phishing doesn’t just affect individuals — it’s also a top threat for businesses.
In the UK, 83% of businesses that suffered cyberattacks in 2022 reported phishing as the attack method. Asian organizations also ranked phishing as the most common attack type in 2021.
These attacks can be incredibly costly.
The average cost of a data breach exceeds $4 million, and high-level “whaling” scams — where executives are targeted — can result in losses of up to $47 million. Millennials and Gen-Z users are particularly vulnerable, and over 20% of phishing emails originate from Russia, showing the global reach of this threat.
Why Are Crypto Users Prime Targets of Phishing?
Crypto transactions are irreversible. If a scammer gets your funds, they’re gone — no refunds, no chargebacks. The decentralized nature of crypto means there’s no safety net or fraud protection like with traditional banks.
Scammers know crypto users juggle wallets, exchanges, DeFi platforms, and NFT marketplaces — creating multiple points of exposure. Every click, every login, and every signature can become an opportunity for attack if not handled with caution.
How Phishing Work
One of the biggest phishing threats in crypto comes from fake smart contracts.
Scammers trick users into signing malicious contracts that grant them unlimited spending permissions, allowing them to drain entire wallets.
These scams often appear in fake airdrops, deceptive dApps, or fraudulent DeFi platforms. Always review contract details before signing and use a trusted wallet that warns against suspicious transactions.
Other tactics include:
- Fake Websites: Clones of legitimate exchanges or wallet apps.
- Customer Support Scams: Impersonated support agents via email, Telegram, or Discord.
- QR Code Phishing (Quishing): Fake codes that lead to credential-stealing sites.
Even cautious users can fall victim, as these scams are often designed to bypass normal security checks and look convincingly real.
From fake login pages to impersonated support teams, scammers employ a variety of methods to steal funds.
Understanding these common types of phishing scams can help you recognize and avoid them before it’s too late.
Common Types of Phishing Scams in Crypto
Cybercriminals use various deceptive methods to trick users into approving transactions or sharing sensitive information. These include fake token approvals, unauthorized transfers, and signature requests disguised as normal actions.
From NFT-related scams to fake captcha pages and spoofed contracts, attackers exploit trust and confusion.

(Source: SlowMist Report)
Learn how to identify these scams is key to protecting your assets.
Essential Crypto Security Checklist: Stay Safe from Phishing Scams
Crypto Phishing scammers are getting smarter, but so can you. Protect your portfolio by staying vigilant and following these essential security steps.
- Check the Sender: Always verify the sender’s email address or phone number before clicking on links or downloading attachments.
- Look for Red Flags: Watch out for urgent requests, spelling errors, and suspicious links.
- Avoid Public Wi-Fi for Crypto Transactions: Hackers can intercept data on unsecured networks. Use a VPN for safe access
- Avoid Clicking on Suspicious Links: Hover over links to check their actual destination before clicking.
- Beware of QR Code Phishing: Scammers use fake QR codes to steal data. Always verify the source before scanning.
- Verify with the Official Source: If an email or message seems suspicious, contact the company directly through their official website or phone number.
- Use Multi-Factor Authentication (MFA): Enable MFA on your accounts for an extra layer of security.
- Never Share Personal Information: Legitimate companies will never ask for sensitive data like passwords via email or text.
- Keep Software Updated: Regularly update your operating system, browser, and security software to protect against vulnerabilities.
- Use a Password Manager: Generate and store strong, unique passwords for each account.
- Be Wary of Unexpected Attachments: Do not open attachments from unknown sources, as they may contain malware.
- Educate Yourself and Others: Stay informed about the latest phishing tactics and help educate friends and colleagues.
- Report Suspicious Emails: If you receive a phishing attempt, report it to your email provider or the appropriate authorities.
Additional Pro Tips for Extra Protection
- Use an Email Spam Filter: This helps block many phishing attempts before they reach your inbox.
- Check for HTTPS: When entering login credentials, ensure the site uses HTTPS and has a legitimate SSL certificate.
- Beware of Social Media Phishing: Scammers often impersonate trusted brands, influencers, or even friends on platforms like Twitter, Telegram, and Discord to trick users into clicking malicious links or sending funds. Always verify official accounts and check trusted sources like the Klever Anti-Scam Page before taking action.
We have also prepared this infographic to help you stay alert and protect yourself from crypto phishing scams.
Save it to your device and refer to it whenever you encounter something suspicious.

(Infographic created with AI)
What to Do If You Get Phished
If you suspect you’ve been phished, take immediate action:
Immediate Steps
- Disconnect your device from the internet to prevent further compromise.
- Move remaining funds to a secure wallet if possible.
- Change all affected passwords and enable stronger 2FA settings.
- Report the attack to your exchange, wallet provider, and cybersecurity agencies.
Long-Term Recovery & Prevention
- Monitor blockchain transactions for suspicious activity.
- Use blockchain forensic services to track stolen funds.
- Warn others in the community to prevent further victims.
Real-World Examples of Phishing Attacks in Crypto
Etherscan Phishing Scam
Etherscan, a popular Ethereum blockchain explorer, has been leveraged by scammers in several phishing schemes.
The core tactic involves impersonating Etherscan’s interface or using its site to deliver malicious prompts.
For example, attackers have injected malicious advertisements or pop-ups on Etherscan’s actual website, prompting users to connect their MetaMask wallets for fake offers (like bogus NFT airdrops)
Scammers have also created clone websites (e.g. using a URL with an extra dash like “et-herscan” in the address) that mirror Etherscan’s appearance.

(In 2024, a sophisticated phishing scam targeted Etherscan users through search engines like DuckDuckGo and Bing – Source: CoinTelegraph)
Once a user clicks such an ad or connects their wallet via a fraudulent prompt, the scammer’s code can initiate a “wallet drainer” smart contract – this lures victims to a fake site and then drains all funds after the wallet is linked
A newly identified attack vector saw the infamous “Angel Drainer” phishing group exploit Etherscan’s contract verification feature.
They deployed malicious code through a Gnosis Safe contract—a multi-signature smart contract wallet on Ethereum that requires multiple approvals for transactions.
By leveraging Etherscan’s verification, they created a false sense of security, tricking users into approving transactions that ultimately drained their funds.
Phishing scams linked to Etherscan led to $300M stolen from 324K users in 2023 and $104M from 97K users in early 2024, with individual losses reaching $300K–$55M. A 215% spike in August 2024 saw 9,100 victims lose $66M through fake ads, clone sites, and malicious contracts.
Ledger Phishing Scams
In July 2020, Ledger, a hardware wallet provider, suffered a major data breach that exposed customer contact information, including email addresses.
Scammers exploited this breach by sending fraudulent emails disguised as official Ledger communications, warning users of a fake security breach.

(Fake Ledger Email – Source: PC Risk)
These emails urged recipients to visit a phishing website and enter their 24-word recovery phrase to ‘secure’ their wallets.
Once obtained, these phrases allowed attackers to gain full access to users’ cryptocurrency wallets.
Quantifying the exact total amount stolen due to these phishing scams is challenging, as many incidents go unreported.
However, specific instances highlight the significant financial impact:
- XRP Theft: In November 2020, over 1.15 million XRP (approximately $280,000 at that time) was stolen from Ledger users through phishing attacks involving fake domains resembling Ledger’s official website.
- December 2023 Incident: A compromised Ledger connector library led to nearly $500,000 in losses, further eroding user trust.
Uniswap Phishing Attack
In July 2022, Uniswap users were targeted in a sophisticated phishing scam that resulted in the theft of over $8 million worth of Ether (ETH).
Attackers sent malicious tokens masquerading as legitimate Uniswap airdrops to approximately 73,399 wallet addresses associated with Uniswap V3 liquidity providers.
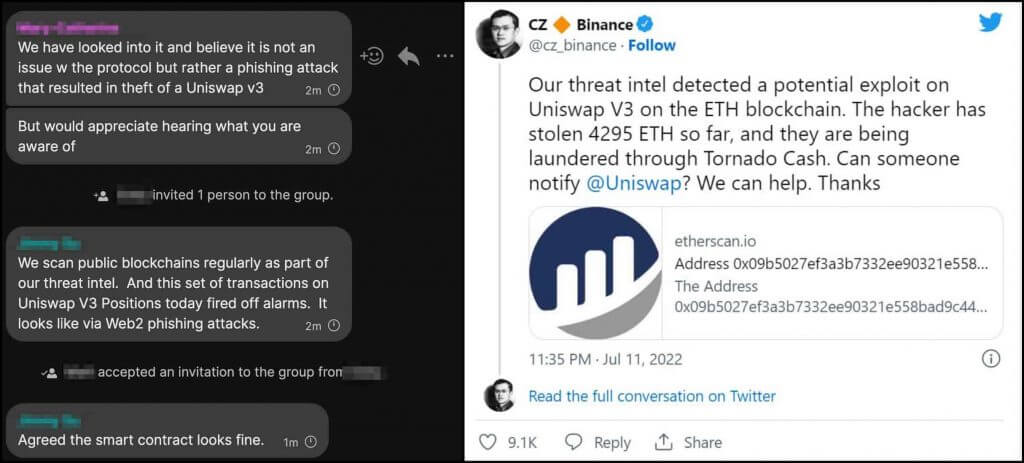
[CZ (Binance’s Former CEO) alerts Uniswap team about phishing hack – Source: Hackread]
These tokens directed recipients to fraudulent websites mimicking Uniswap’s interface, prompting users to connect their wallets and sign transactions.
Unknowingly, victims granted the attackers full access to their wallets, leading to significant financial losses.
Metamask Phishing Scams
MetaMask users have been frequently targeted by scammers posing as support representatives, exploiting social media platforms like Twitter, Telegram, and Discord.
These fraudsters contact users, offering fake assistance and requesting private keys or seed phrases under the guise of ‘verifying accounts’ or ‘fixing issues.’ Once obtained, attackers drain victims’ wallets, leaving no chance of fund recovery. Always verify the authenticity of any website or application before entering sensitive information.
One of the most sophisticated attacks occurred in 2024, when scammers leveraged fake Google Play ads to promote cloned MetaMask wallet apps. Unsuspecting users who downloaded these fraudulent apps and entered their seed phrases unknowingly surrendered full control of their funds.
Despite MetaMask’s repeated warnings and security advisories, attackers continued registering new domains and distributing fake apps to evade detection.

(Scammers ask the victims to verify their accounts using fake Metamask email – Source: Kaspersky)
Neither MetaMask, Ledger, Uniswap, nor Klever Wallet will ever contact users to request their seed phrase or private keys. Stay vigilant!

(Fake MetaMask site phishing for wallet recovery phrases; note the suspicious URL – Source: Kaspersky)
Stay Vigilant, Stay Safe
Phishing attacks will continue evolving, but with awareness and caution, you can protect yourself from falling victim.
Remember to take these simple steps to protecting yourself from Phishing Attacks:
- Stay safe on public Wi-Fi: Avoid using public Wi-Fi networks for sensitive activities.
- Double-check URLs and email addresses: Before clicking any links, verify the URL or email address to ensure it’s legitimate.
- Use two-factor authentication (2FA): Enable 2FA apps for an extra layer of security on your accounts.
- Keep software updated: Regularly update your software to patch security vulnerabilities.
- Protect your seed phrase: Never share your 24-seed phrase with anyone.
- Be wary of offers that seem too good to be true: If an offer seems suspicious, it’s likely a scam.
Think Before You Click. Protect Before You Lose.




