
Crypto Scams
The cryptocurrency industry has always been a fertile ground for innovation, but with opportunity comes risk. In just the first two months of 2025, the crypto space has witnessed an alarming surge in scams, rug pulls, and hacks, leading to billions in losses.
The largest crypto heist in history has already occurred, involving the Bybit hack, and a series of celebrity-endorsed rug pulls have left thousands of participants at a loss.
Fraudulent activities are evolving, and staying informed is crucial for anyone engaging with crypto assets.
This article is the first in our “Crypto Fraud Awareness” series, aiming to bring awareness to major fraudulent activities, dissect their mechanics, and provide actionable steps for you to protect your portfolio.
We will explore key scams of the crypto market, emerging trends in fraud, and best practices for keeping your digital assets secure.
Stay Safe!
The Scope of Crypto Crime in 2024
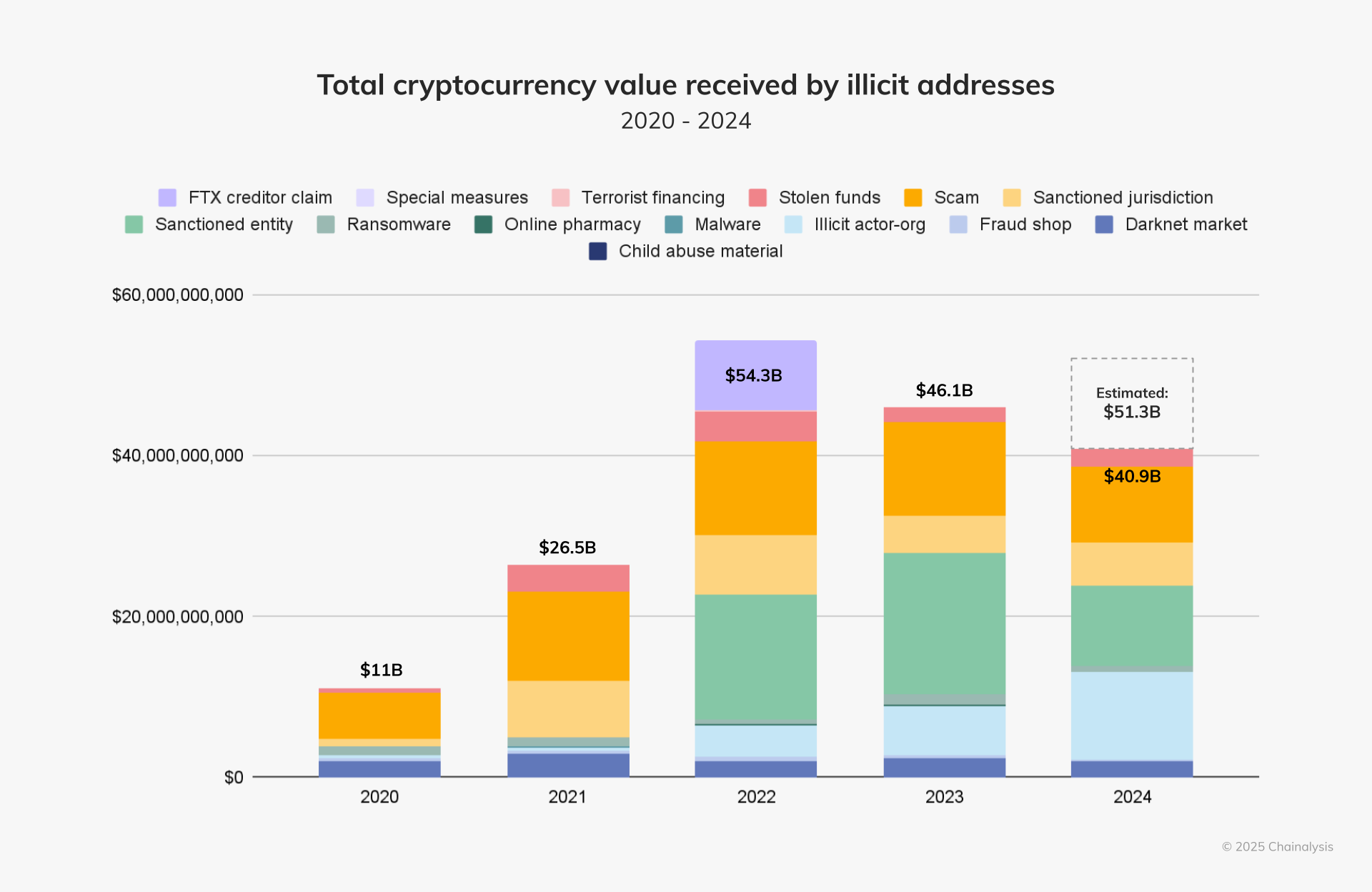
According to Chainalysis data, $40.9 billion in cryptocurrency was received by known illicit addresses in 2024. However, estimates suggest that the actual total could be closer to $51 billion, given historical trends of delayed fraud detection.
Despite this, illicit transactions accounted for only 0.14% of total on-chain transaction volume, significantly lower than 0.61% in 2023.
(Source: ChainAnalysis)
Chainalysis reports a year-over-year decline in absolute illicit transaction volume but expects the numbers to rise as additional data surfaces. Historically, the percentage of crypto activity linked to crime remains below 1% of total market volume.
The Biggest Crypto Scams of 2025 So Far
According to recent insights reported by Foresight News, the cryptocurrency market faced notable losses totaling around $98.19 million in just the first month of 2025.
SlowMist, a cybersecurity analytics firm, documented approximately 40 individual hacking events during this timeframe, causing a combined financial impact of nearly $87.94 million.
Although cybersecurity teams managed to reclaim about $1.47 million, the majority remains unrecovered. Additionally, Scam Sniffer, another prominent crypto anti-scam platform, identified an alarming number of approximately 9,220 individual victims, contributing an additional $10.25 million in losses.
These figures underline the ongoing security challenges within web3 and highlight the urgency for enhanced protective measures and user vigilance.
1. The Bybit Hack: A Record-Breaking Heist ($1.5 Billion)

(Source: Bybit)
On February 21, 2025, Dubai-based cryptocurrency exchange Bybit suffered a devastating hack, losing $1.5 billion worth of Ethereum (ETH). This breach has been classified as the largest crypto theft in history. The attack occurred during a routine transfer of funds from a cold wallet to a warm wallet, at which point hackers exploited a vulnerability, gaining unauthorized access and draining the assets.
Who Was Behind the Bybit Hack?
Blockchain forensic experts, including Arkham Intelligence, have linked this massive breach to North Korea’s Lazarus Group, a state-sponsored hacking organization responsible for multiple high-profile cyber crimes. They used forged digital signatures and chain-hopping techniques to obscure the movement of stolen funds, making them harder to track.
Bybit’s Response & Market Impact
Bybit CEO Ben Zhou assured customers that the exchange remains financially solvent and has since purchased $1.2 billion in Ethereum to replenish customer accounts. Despite this reassurance, the hack sent shockwaves through the crypto market, triggering a 4.8% drop in ETH prices, while other major cryptocurrencies like Bitcoin and Solana also saw declines.

(Crypto Market response to Bybit hack – Source: Coin360)
2. The Phemex Exchange Breach ($85 Million)
On January 23, 2025, Phemex, a major cryptocurrency exchange, suffered a security breach that led to the theft of $85 million in digital assets. The attack targeted Phemex’s hot wallets, initially estimated at $29 million in losses but later revised upwards by security firms as more compromised transactions were uncovered.
Connection to the Bybit Hack
Blockchain investigators, including Arkham Intelligence and ZachXBT, have linked the Phemex hack to the same North Korean Lazarus Group responsible for the $1.5 billion Bybit hack. On February 22, 2025, ZachXBT confirmed on X that Lazarus Group-affiliated wallets had commingled funds from both incidents, proving a direct connection.

(North Korea hacking activity. Source: Chainalysis)
On-chain data shows that Phemex’s hot wallets were drained across 125 transactions, spanning 11 blockchain networks, including:
The stolen funds were then laundered through Tornado Cash, a privacy-focused DeFi protocol on Ethereum, making them difficult to trace
Response & Money Recovery
Phemex immediately:
- Suspended deposits and withdrawals to prevent further damage.
- Engaged third-party security firms to investigate the breach.
- Confirmed it had sufficient reserves to cover all user funds.
- Rolled out a compensation plan for affected participants.
Despite the exchange’s reassurance, the attack heightened concerns over state-backed hacking groups exploiting centralized exchange vulnerabilities.
Over the past year, North Korean hackers have been linked to several major crypto heists, including the $305 million DMM Bitcoin hack, $50 million Upbit hack, $50 million Radiant Capital hack, and $16 million Rain Management hack, according to a joint statement from global authorities
3. The AdsPower Malware Attack ($4.7 Million)

(Source: NewsRisky)
Between January 21-24, 2025, AdsPower, a company specializing in anti-detect browser technology, suffered a cyberattack that led to the theft of $4.7 million in cryptocurrency. Attackers compromised AdsPower’s distribution system, replacing a legitimate browser plugin with a malicious version that infected users’ devices.
For three days, users who downloaded or updated the plugin unknowingly installed malware that allowed the attackers to steal mnemonic phrases and private keys. Ultimately, five wallets were compromised. This attack highlights the risk of off-chain vulnerabilities, even when software appears to be from a trusted source.
4. The Moby DeFi Exploit ($2.5 Million)
On January 8, 2025, Moby, an options trading platform operating on the Arbitrum network, was compromised due to a leaked private key. Hackers exploited this vulnerability by activating an emergency withdrawal function, draining a total of $2.5 million in USDC, Wrapped Ethereum (WETH), and Wrapped Bitcoin (WBTC).

(Whitehat Hacker Tony K post – Source X)
Whitehat Recovery Efforts
In a notable twist, whitehat hacker Tony Ke from Solayer Labs quickly intervened, identifying a critical vulnerability left by the attackers. He managed to reclaim approximately $1.5 million in USDC, significantly reducing the impact and limiting the final losses by around 60%. Despite these efforts, the remaining stolen funds—amounting to roughly $1 million—are still unrecovered, demonstrating the persistent vulnerabilities and complexities in decentralized finance (DeFi).
While centralized platforms like Bybit and Phemex have suffered massive breaches and even reputable software like AdsPower has been compromised, decentralized finance (DeFi) platforms aren’t immune to vulnerabilities either.
The Moby DeFi exploit further underscores the importance of recognizing security risks across all layers of the crypto ecosystem.
The high-profile breaches and sophisticated attacks we’ve examined are dramatic examples, but they’re just the tip of the iceberg.
Scammers are relentless, adapting their tactics to exploit every possible weakness—whether in exchanges, DeFi protocols, or even trusted software.
The cases we’ve covered are just the beginning; crypto scams come in many forms, each designed to deceive unsuspecting users.
Would you spot one before it’s too late? Let’s find out.
Most common types of crypto scams to be aware of

(Source: Freepik)
Cryptocurrency scams come in many forms, exploiting technology, human psychology, and security loopholes to deceive participants. From phishing schemes and rug pulls to sophisticated exchange hacks, fraudsters continue to evolve their tactics, making it essential to understand the most common types of crypto scams and how to recognize them.
1. Phishing Scams

(Source: Ledger)
What are Phishing Scams?
Phishing scams are deceptive attempts using fake emails, messages, or websites designed to trick users into revealing sensitive information, such as login credentials or private keys.
Example: Fraudulent wallet or exchange login pages impersonating reputable platforms, such as the Ledger Phishing Attack (2020).
2. Rug Pulls
What are Rug Pulls?
Developers, celebrities and most recently, political figures create hype around a crypto project, raise funds, and then cash out or disappear, leaving holders with worthless tokens.

(Source: X)
Example: Hawk Tuah memecoin (2024) and other DeFi projects, like $LIBRA endorsed by Argentina’s President Milei and $MELANIA coins, that vanish overnight.
3. Ponzi and Pyramid Scheme
What are Ponzi and Pyramid Schemes ?
Fraudulent schemes where earlier participants are paid with funds from new participants rather than legitimate revenue.

(Source: Shutterstock)
Example: High-yield staking or lending platforms that collapse when new deposits stop, such as OneCoin and BitConnect Schemes
4. Pig Butchering Scams
What are Pig Butchering Scams?
A long-term deceptive tactic where scammers gradually build trust and relationships with victims, enticing them into what appear to be legitimate cryptocurrency opportunities. Victims deposit funds into apps or accounts secretly controlled by scammers, who promise increasing returns to encourage further deposits.

(Source: ABC7NY)
Example: The Kansas Bank CEO Pig Butchering Scam ($47M in 2024).
5. AI-Powered Deepfake Giveaway Scams on Social Media
What are AI-Powered Deepfake Giveaway Scams on Social Media?
Social Media Giveaway Scams involve fraudsters impersonating celebrities or public figures to promote fake giveaways promising to double the amount of cryptocurrency sent by users—but never returning the funds.
With advances in artificial intelligence, scammers have enhanced these frauds using deepfakes—AI-generated fake videos or audio—to make their scams even more convincing.
Criminals use deepfake versions of public figures to endorse fraudulent crypto investments. For example, deepfake videos featuring personalities like Taylor Swift, Tom Hanks, and Oprah Winfrey have been leveraged to deceive users into fake investment schemes.

(Source:Cryptopolitan)
Example: In 2020, scammers impersonated figures such as Elon Musk and Vitalik Buterin in a Twitter-based giveaway scam, resulting in losses totaling approximately $100,000.
In early 2025, deepfake videos of Singapore’s Prime Minister Lawrence Wong circulated online, praising cryptocurrency investments and prompting authorities to issue public warnings about these deceptive practices.
6. Exchange & Wallet Hacks

(Source: DepositPhotos)
What are Exchange & Wallet Hacks?
Cybercriminals exploit vulnerabilities in crypto exchanges or wallets to steal funds.
Example: The Bybit Hack ($1.5B in 2025), Phemex Hack ($85M in 2025).
7. Ransomware Attacks
What are Ransomware Attacks?
Malicious software attacks that encrypt victims’ data, demanding cryptocurrency payments for restoring access.

(Source: Cyberhook)
Example: Attackers encrypt critical files or systems, often targeting hospitals or government institutions, and demand Bitcoin payments, as seen in the Colonial Pipeline Ransomware Attack (2021).
8. Smart Contract Exploits
What are Smart Contract Exploits?
Hackers manipulate vulnerabilities in smart contracts to drain liquidity from DeFi projects.

(Source: Revoke)
Example: The Moby DeFi Exploit ($2.5M in 2025).
9. Malware & Fake Softwares
What are Malware & Fake Softwares ?
Fraudsters inject malware into legitimate-looking apps or browser extensions to steal private keys.
Example: The AdsPower Malware Attack ($4.7M in 2025).
10. Insider Trading & Market Manipulation
What are Insider Trading & Market Manipulation?
Crypto project insiders manipulate token prices for personal gain.
Example: Founders of a project pre-mining tokens and selling at peak prices, like the Coinbase Insider Trading Scheme (2022)
11. Dusting Attacks
What are Dusting Attacks?
Scammers send tiny amounts of cryptocurrency to wallets to track transactions and de-anonymize users.
Example: Attackers use dusted funds to link multiple wallet addresses to one owner.
12. Address Poisoning
What is an Address Poisoning Attack?
Scammers use automated tools to identify active wallet addresses, like yours, and send small amounts of cryptocurrency to create a misleading transaction history. Their goal is to trick you into accidentally copying their fake address from your history, causing you to send funds to the scammer.

(Source: Klever Wallet Archive)
Example: You might receive tiny amounts of TRX in your Klever Wallet from an address similar to your own, increasing the chance you’ll copy this fake address by mistake. Always double-check the full address carefully—stay safe!
13. Fake ICOs (Initial Coin Offerings)
What are Fake ICOs (Initial Coin Offerings)?
Fraudulent startups raise funds for a token that is never developed or launched, or later revealed as a Ponzi Scheme.
Example: Projects that vanish after raising millions through pre-sales. The BitConnect Scam (2016-2018), where the platform promised high returns through a trading bot, leading to significant investor losses when it was exposed as a Ponzi scheme.
14. Crypto Pump-and-Dump Schemes
What is a Crypto Pump-and-Dump Scheme?
Coordinated efforts to artificially inflate a token’s price, luring traders before insiders sell at the peak.

(Source: News18)
Example: Low-cap tokens promoted via Telegram or Discord groups. The Squid Game Token Pump-and-Dump Scam (2021) was a clear pump-and-dump scheme.
15. SIM-Swap Attacks
What are SIM-Swap Attacks?
Hackers hijack a victim’s phone number to gain control over crypto accounts.
Example: Attackers trick mobile carriers into transferring phone numbers. The Michael Terpin SIM-Swap Attack ($20M in 2018).
16. Fake Investment Platforms
What are Fake Investment Platforms?
Fraudulent websites promising guaranteed high returns on crypto deposits.
Example: Fake mining platforms or auto-trading bots. The OneCoin Ponzi Scheme ($4 billion, 2014-2016).
17. Exchange Exit Scams
What are Exchange Exit Scams?
Fraudulent schemes where centralized cryptocurrency exchanges suddenly shut down operations, disappearing with users’ funds.

(Credits: Stephanie Keith – Bloomberg)
Example: The FTX Collapse ($8 Billion, 2022).
18. YouTube Comment Seed Phrase Scam
What is the Youtube Seed Phrase Scam?
A deceptive crypto scam where fraudsters post seemingly legitimate seed phrases in the comment sections of YouTube videos or social media platforms. These posts bait users into accessing cryptocurrency wallets that appear to contain substantial funds, but they are actually traps designed to steal assets.

(Source: Kaspersky)
Examples:
- Kaspersky Research (2024): Reports indicate an increase in YouTube-based seed phrase scams, with scammers luring victims into wallets requiring a secondary transaction, only to drain their funds once a deposit is made.
- Crypto Security Alerts (2023-2025): Multiple victims have reported being tricked into believing they found an abandoned crypto wallet, only to lose their own funds when attempting to withdraw.
How to Protect Yourself from Crypto Scams
- Verify crypto projects thoroughly: Check credentials, audits, and liquidity transparency. Watch out for wallets controlling large portions of a token supply.
- Avoid high-return promises: Skepticism protects against falling into schemes. No legitimate crypto platform guarantees returns. If a platform relies on new user inflows to pay previous participants, it’s likely a Ponzi scheme.
- Enhance security: Use hardware wallets, multi-factor authentication, and safeguard private keys and seed phrases.
- Stay informed: Follow reputable sources and engage with crypto security communities.
What if You’ve Already Fallen Victim to a Scam?
- Report immediately: Contact the affected platform or exchange to report the incident.
- Collect evidence: Save all possible evidence, such as wallet addresses, screenshots, and any scam-related communications.
- Report to authorities: Notify relevant law enforcement agencies and provide all the documentation you have.
- Warn the community: Share your experience with crypto communities to help others avoid similar scams.
Stay one step ahead of scams—secure your crypto portfolio with Klever Wallet and enhance protection using KleverSafe, the trusted cold wallet solution.
Take control today and experience safer crypto management with a Klever Wallet.
Be your own bank – Be Klever!




