
Imagine updating a trusted library in your project and, without realizing it, installing malware designed to steal cryptocurrencies. That was the scenario in September 2025, during the NPM supply chain attack, when hackers compromised 18 of the most popular NPM packages.
These libraries are downloaded more than 2 billion times per week, powering applications, businesses, and developer tools worldwide.
In this article, you’ll learn how the attack happened, what its impact could have been on the JavaScript ecosystem and the crypto market, and the key security measures to reduce risks.
What Is a Supply Chain Attack?
A supply chain attack happens when hackers compromise tools and dependencies widely used by developers.
NPM (Node Package Manager) is a tool used to manage and import packages.
Instead of attacking a company directly, criminals insert malicious code into trusted libraries, such as these NPM packages or similar managers
When these libraries are updated or downloaded, the malware spreads to projects, applications, and corporate systems, exposing thousands of users to invisible risks.
How the 2025 NPM Supply Chain Attack Was Carried Out

Source: Github/Burnett01
- Phishing Against Maintainer
The entry point was a fake NPM support email sent to developer Josh Junon (qix). The domain used was almost identical to the official one, tricking him into providing his username, password, and 2FA code.
- Credential Theft
With these details, the attacker took over the maintainer’s legitimate account, gaining full access to publish packages on the NPM repository.
- Malicious Uploads
The attacker then released infected versions of 18 popular packages, such as chalk and debug. Together, these packages account for more than 2 billion weekly downloads, amplifying the global impact.
- “Crypto-Clipper” Malware Injection
The injected code targeted cryptocurrency transactions across multiple blockchains, including Ethereum and Solana. It worked as follows:
- Intercepted web crypto activity and hooked into browser APIs.
- Monitored and altered network responses.
- Replaced wallet addresses with attacker-controlled addresses.
Unlike other malware, it only activated during transaction approvals, which made immediate detection more difficult.
Potential Impacts of the NPM Supply Chain Attack
Risk to the JavaScript Ecosystem
- Critical libraries like chalk, strip-ansi, and color-convert could have spread malware to millions of applications.
- The attack would have affected everything from personal websites to government and financial systems, shaking trust in open source.
- This includes not only personal apps and websites but also critical corporate infrastructures such as financial, healthcare, and even government systems that rely on these dependencies.
Direct Impact on the Crypto Market
- The code acted as a crypto-clipper, a type of malware designed to silently steal cryptocurrencies by intercepting transactions on blockchains such as Ethereum and Solana.
- Users could authorize legitimate transactions, only to have their funds silently redirected to wallets controlled by attackers.
- It is estimated that billions of dollars in value could have been at risk if exchanges, software wallets, and popular dApps had been running malicious versions of the libraries.
Collapse of Trust in Software Wallets and dApps
- If the attack had succeeded on a large scale, digital wallets and dApps built on top of the compromised libraries would have immediately come under suspicion.
- This could have triggered a mass migration of users to hardware wallets and drastically reduced adoption of Web3 solutions that depend on browsers.
Consequences for Companies and Developers
- Large-scale CI/CD pipeline failures, disrupting development workflows for thousands of teams.
- Companies could face direct financial losses, lawsuits, and even regulatory penalties for negligence in code auditing.
- NPM’s reputation as essential web infrastructure would be severely damaged.
Regulatory and Market Repercussions
- International security standards for open source could be fast-tracked.
- In the crypto sector, confidence in DeFi would likely drop, affecting liquidity and token prices.
Why Did the NPM Supply Chain Attack Fail?
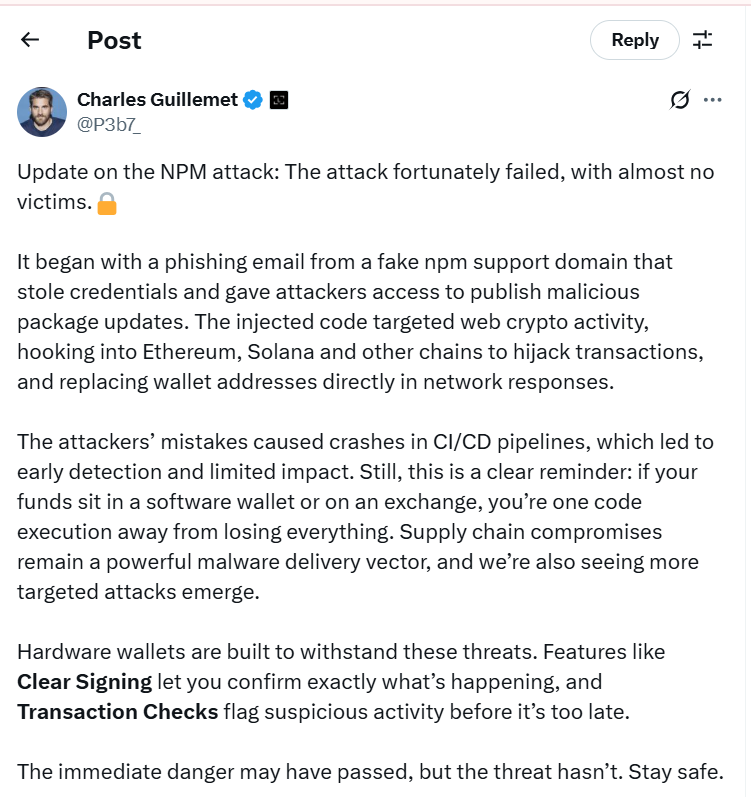
Source: X
The September 2025 NPM attack could have been devastating, but it was stopped in time. Thanks to quick detection, the incident resulted in almost no victims and minimal financial losses.
The attackers made mistakes. Their malicious updates caused crashes in CI/CD pipelines, which quickly raised red flags among developers. The compromised versions were removed within hours, greatly limiting the damage.
Why NPM Attack Matters?
The attack proved how a single phishing email can compromise an entire software supply chain. By gaining access to one maintainer’s account, hackers managed to manipulate libraries used by millions of apps and businesses across multiple industries.
In the crypto space, the risk was even more serious: digital wallets (software wallets) and dApps built on the compromised libraries could have had funds silently redirected to attacker-controlled wallets.
Even with limited financial impact, the case demonstrated that just one poisoned package is enough to spread malware globally in a matter of minutes.
For users and businesses, the takeaway is clear: software wallets and online exchanges carry ongoing risks because they depend on updates that can be exploited. In contrast, hardware wallets remain the safest option, thanks to features like Clear Signing (step-by-step transaction confirmation) and Transaction Checks (flagging suspicious activity).
Key Lessons for Developers and Users
- Always check the destination address before confirming a transaction.
- Use hardware wallets whenever possible for high-value cryptocurrency transactions, and use hot wallets for smaller amounts
- Use hardware wallets whenever possible for cryptocurrency transactions.
- Stay highly alert against phishing attempts targeting developer credentials.
- Adopt runtime protection tools (e.g., ADR) to detect malicious behavior inside applications.
NPM Supply Chain Attack 2025: A Global Wake-Up Call on Digital Security and Cryptocurrencies
The 2025 NPM supply chain attack was a powerful reminder that digital security starts even before a single line of code is executed. Compromised dependencies can quickly escalate into global crises, affecting millions of users and undermining trust across the entire software and crypto ecosystem.
For developers, companies, and end users, the lesson is clear: auditing dependencies, adopting anti-phishing best practices, and strengthening digital wallet security are not optional, they are essential.
Stay informed, update your security processes, and protect your cryptocurrencies with the best practices.




