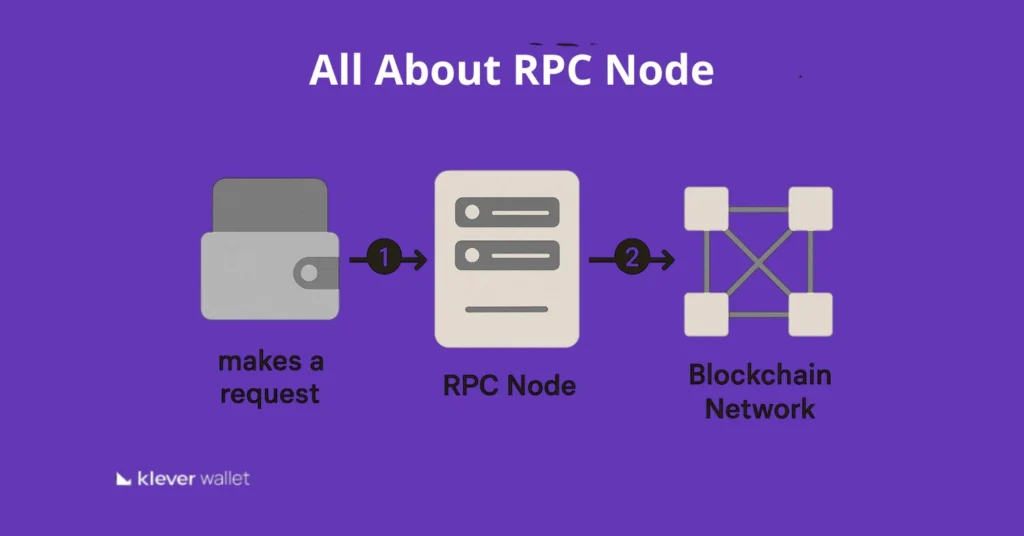
Hey crypto friends!
The cryptocurrency market is one that has always been exposed to risks and threats due to its infancy and the lack of public knowledge about this technology. Some of the major risks in this market are scams and cyber invasions. With the advancement of technology, new methods of fraud have emerged that can have very serious consequences for cryptocurrency market users.
Generally, no reputable company will send a private message for guidance and support on any social network. You should follow information related to product support from a company’s own reliable sources. Support for Klever products is available at the link: https://support.klever.io/hc/en-us/requests/new
To avoid this type of scam, it is necessary for users of this market to employ security techniques that reduce their risk when using the wallet to perform various tasks, which can be mentioned as follows:
How to maintain security with your cryptocurrencies and avoid hacks
Private Messages
Klever will never reach out via private message. Always seek the original source to support the company’s products.
Cracked Software
Using free and cracked software will diminish the security of the device you are using. Always strive to use genuine software.
Free VPNs
Utilizing free VPNs increases the risk of communicating and maintaining security information on your device.
dApps (Decentralized Applications based on blockchains)
The use of decentralized sites to interact with different blockchains should always be considered. Due to their decentralized nature, anyone with programming knowledge is capable of creating these decentralized programs for specific purposes.
Wallet Access to Decentralized Applications (Approval)
Access to your wallet should always be verified at different intervals, and it is advisable to never have unlimited access to smart contracts. Even valid and approved decentralized programs are not exempt and can be targeted by certain individuals or groups.
Recognize Phishing Attempts
Be wary of phishing emails or messages attempting to impersonate legitimate services or exchanges. Always verify the URLs and never click on suspicious links. Legitimate companies do not request your private keys or confidential information via email.
Hardware Wallets
For added security, it is definitely recommended to use hardware wallets, but if you have sufficient experience in the area of using multi-signature wallets, it can be a good alternative to hardware wallets.
Be cautious with public Wi-Fi networks
Avoid accessing your encrypted wallets or conducting transactions on public Wi-Fi networks, as they can be insecure and susceptible to interception by cybercriminals.
Backup your wallets
Safely backup your wallet data, including recovery phrases or initial keys, in multiple secure locations. This ensures that you can regain access to your assets even if your primary device is lost or damaged.
By implementing these strategies, you can significantly reduce the risk of falling victim to scams and ensure the security of your cryptocurrencies in the constantly evolving digital landscape.
5 Strategies to Maximize Your Cryptographic Security
1. Use Hardware Wallets for Cold Storage
Hardware wallets provide unparalleled security for your cryptocurrency holdings. Unlike software wallets that are susceptible to online threats, hardware wallets store your private keys offline. This method, known as “cold storage,” ensures your cryptocurrencies are secure even in the face of internet-based attacks.
Studies indicate that the use of hardware wallets significantly reduces the risk of cryptocurrency theft, as it requires physical access to the device to execute transactions. This layer of security is essential for anyone serious about safeguarding their digital assets.
2. Enable Two-Factor Authentication (2FA)
Activating two-factor authentication across all exchange platforms and wallets adds a critical layer of security. This method requires not only your password but also a code generated on a device you own, making unauthorized access vastly more difficult, even if your password is compromised.
There are various forms of 2FA, including SMS messages, authenticator apps like Google Authenticator, and hardware tokens. The choice depends on your preference and the options provided by the platform, but any form of 2FA is better than none.
3. Stay Educated and Aware
The landscape of cryptocurrency is ever-changing, with new scams and threats emerging regularly. Staying informed about the latest security practices and common scam types can protect you and your assets. Engaging with forums, reading specialized blogs, and attending webinars are great ways to stay ahead.
4. Regular and Secure Backup of Private Keys
Your private keys are the only way to access your cryptocurrencies. Without them, your assets could be lost forever. Perform regular backups of your keys and store them in multiple secure locations. Using physical mediums like paper or metal for recording your keys provides durable protection against digital failures like hard drive crashes or cyber-attacks.
5. Utilize Multi-Signature (Multisig) Accounts
Multisig accounts require more than one private key to authorize a cryptocurrency transaction. This is an excellent strategy for businesses or investors seeking an extra layer of approval for their transactions, ensuring no action is taken without the consent of all parties involved.
Klever Security Key

Your security key or 24 seed-phrase, the foundation of your digital wallet’s security, is generated randomly. This randomness is crucial to ensure that each user’s phrase is unique and virtually impossible to replicate or guess.
If someone sends you a message, email, or even calls, claiming to be a Klever employee, or not, and asking for the 24 seed-phrase, do not send it. Our team will never ask for this access, which is solely and exclusively yours. We do not take responsibility for losses or theft of this key, which is why we always emphasize to our users the importance of keeping it secure.
Learn more about in the article “Consequences of Losing Your Cryptography Recovery Phrase.”
The most common scams in the crypto world
Unrealistic Arbitrage Opportunities
Scammers may promote schemes promising risk-free profits by exploiting price differences across multiple cryptocurrency exchanges. While arbitrage is a legitimate strategy, the “guaranteed” and significant returns with minimal effort advertised by fraudulent schemes are highly suspicious.
Initial Coin Offering Frauds
Enthusiasts are enticed to purchase new tokens with the promise of being the next Bitcoin or Ethereum in terms of growth. However, many of these projects lack a solid foundation or are outright scams designed to collect funds without providing any real value.
Pump and Dump Schemes
Scammers artificially hype up a less popular cryptocurrency by spreading false or misleading information to inflate its price. When the price is high enough and they convince enough people to buy, they sell off their entire stake in the cryptocurrency at that inflated price. When they cash out, the price drops, and most new buyers are left with a cryptocurrency now worth a fraction of what they paid, leading to losses for those who did not participate in the scheme.
Decentralized finance (DeFi)
Developers may create a new project that retains a substantial amount of investors’ funds, only to “rug pull” by withdrawing all liquidity, leaving investors with worthless tokens.
Ransomware
Cryptographic ransomware scams occur when hackers take control of the victim’s device or account using malicious software, encrypt it, and demand payment in cryptocurrency for the decryption key.
Blackmail
Scammers contact the victim claiming to have embarrassing personal information, including private photos or videos, which they threaten to make public if their demands are not met. Typically, these scammers promise to keep this information private if the victim sends a cryptocurrency transfer immediately.
Fake ICOs
Scammers can create and promote fake ICOs, convincing investors to buy tokens for a nonexistent or entirely fraudulent project and then disappear with the funds.
Giveaways
Fraudsters impersonate legitimate cryptocurrency exchanges, companies, or notable individuals to trick victims into sending them cryptocurrencies. They typically promise to return double or triple the amount sent by the victim—only to disappear with the funds after receiving them.
Cryptojacking
Cryptojackers are scammers who secretly use your computing device to mine cryptocurrencies without your knowledge. Cryptojackers aim to reap all the benefits of cryptocurrency mining without any expense, while you are left with an energy-consuming and poorly functioning device.
Fake Wallets
A fake wallet scam deceives users into believing they are using a legitimate digital wallet to store their assets. The fake wallet prompts users to enter their private keys—information that should never be shared—and then scammers use these private keys to steal users’ cryptocurrency holdings.
Learn More about Klever Wallet and download now!